17
brew China mirrors
China blocks git, so we need to use mirrors for brew.sh install
Tsinghua and Aliyun both host mirrors. Aliyun seems faster, so we will use that below.
USTC Mirror – https://mirrors.ustc.edu.cn/help/brew.git.html
Aliyun Mirror – https://mirrors.aliyun.com/homebrew/
#install brew from ustc
/bin/bash -c “$(curl -fsSL https://mirrors.ustc.edu.cn/misc/brew-install.sh)”
#install tap for brew cask upgrade mirror
brew tap –custom-remote –force-auto-update buo/cask-upgrade https://gitcode.com/gh_mirrors/ho/homebrew-cask-upgrade/
#set aliyun mirror for brew and update
export HOMEBREW_INSTALL_FROM_API=1
export HOMEBREW_API_DOMAIN=”https://mirrors.aliyun.com/homebrew-bottles/api”
export HOMEBREW_BREW_GIT_REMOTE=”https://mirrors.aliyun.com/homebrew/brew.git”
export HOMEBREW_CORE_GIT_REMOTE=”https://mirrors.aliyun.com/homebrew/homebrew-core.git”
export HOMEBREW_BOTTLE_DOMAIN=”https://mirrors.aliyun.com/homebrew/homebrew-bottles”
brew update
#alternately use ustc
export HOMEBREW_BREW_GIT_REMOTE=”https://mirrors.ustc.edu.cn/brew.git”
export HOMEBREW_CORE_GIT_REMOTE=”https://mirrors.ustc.edu.cn/homebrew-core.git”
export HOMEBREW_BOTTLE_DOMAIN=”https://mirrors.ustc.edu.cn/homebrew-bottles”
export HOMEBREW_API_DOMAIN=”https://mirrors.ustc.edu.cn/homebrew-bottles/api”
brew update
#add aliyun mirror permanently into zsh
echo ‘export HOMEBREW_INSTALL_FROM_API=1’ >> ~/.zshrc
echo ‘export HOMEBREW_API_DOMAIN=”https://mirrors.aliyun.com/homebrew-bottles/api”‘ >> ~/.zshrc
echo ‘export HOMEBREW_BREW_GIT_REMOTE=”https://mirrors.aliyun.com/homebrew/brew.git”‘ >> ~/.zshrc
echo ‘export HOMEBREW_CORE_GIT_REMOTE=”https://mirrors.aliyun.com/homebrew/homebrew-core.git”‘ >> ~/.zshrc
echo ‘export HOMEBREW_BOTTLE_DOMAIN=”https://mirrors.aliyun.com/homebrew/homebrew-bottles”‘ >> ~/.zshrc
source ~/.zshrc
#update brew, casks
brew update; brew upgrade; brew cu -af;
Journalctl keeps logs on the servers for systemd.
The default settings can lead to too much disk space use. Logs are good to have, but the default settings are unlimited, and if you do not watch out they can get up to gigabytes in size. A more reasonable default is 100M, as this will still allow you to debug any non-running systemd scripts and not take up too much valuable disk space.
To reduce journalctl disk usage, we can clean up the un-needed logs, and optionally reduce the disk space needed to keep logs.
To Show disk usage:
journalctl --disk-usageTo clean up disk usage (to 100M in size):
journalctl --vacuum-size=100MTo make this the default for future, we can edit the systemd journald settings and set the logs to a more reasonable size.:
pico /etc/systemd/journald.conf
//Uncomment the SystemMaxUse line and set to 100M
SystemMaxUse=100M
//Save and exit CTRL O, CTRL X, Enter to save
//Finally restart systemd
systemctl restart systemd-journald
Note: Logs can be seen by checking one of the running services. These usually sit in /etc/systemd/system or /etc/systemd/user.
e.g. to check php 8.3 fpm service logs
journalctl -xeu php8.3-fpm.service
19
qmail-dkim settings
As I can never find this online, and man -l /var/qmail/man/man8/qmail-dkim.8 is a pain, I’ve posted the DKIM settings below.
—
The complete set of letters with the corresponding return status is given below
A – DKIM_SUCCESS – Function executed successfully
B – DKIM_FINISHED_BODY – process result: no more message
body is needed
C – DKIM_PARTIAL_SUCCESS – verify result: at least one
but not all signatures verified
D – DKIM_NEUTRAL – verify result: no signatures
verified but message is
not suspicious
E – DKIM_SUCCESS_BUT_EXTRA – signature result: signature
verified but it did not
include all of the body
F – DKIM_3PS_SIGNATURE – 3rd-party signature
G – DKIM_FAIL – Function failed to execute
H – DKIM_BAD_SYNTAX – signature error: DKIM-Signature
could not parse or has bad
tags/values
I – DKIM_SIGNATURE_BAD – signature error: RSA verify
failed
J – DKIM_SIGNATURE_BAD_BUT_TESTING – signature error: RSA verify
failed but testing
K – DKIM_SIGNATURE_EXPIRED – signature error: x= is old
L – DKIM_SELECTOR_INVALID – signature error: selector doesn’t
parse or contains invalid values
M – DKIM_SELECTOR_GRANULARITY_MISMATCH – signature error: selector
g= doesn’t match i=
N – DKIM_SELECTOR_KEY_REVOKED – signature error: selector
p= empty
O – DKIM_SELECTOR_DOMAIN_NAME_TOO_LONG – signature error: selector domain
name too long to request
P – DKIM_SELECTOR_DNS_TEMP_FAILURE – signature error: temporary dns
failure requesting selector
Q – DKIM_SELECTOR_DNS_PERM_FAILURE – signature error: permanent dns
failure requesting selector
R – DKIM_SELECTOR_PUBLIC_KEY_INVALID – signature error: selector
p= value invalid or wrong format
S – DKIM_NO_SIGNATURES – no signatures
T – DKIM_NO_VALID_SIGNATURES – no valid signatures
U – DKIM_BODY_HASH_MISMATCH – sigature verify error: message
body does not hash to bh value
V – DKIM_SELECTOR_ALGORITHM_MISMATCH – signature error: selector
h= doesn’t match signature a=
W – DKIM_STAT_INCOMPAT – signature error: incompatible v=
X – DKIM_UNSIGNED_FROM – signature error: not all message’s
From headers in signature
For example, if you want to permanently reject messages that have a signature that is expired, include the letter ‘K’ in the DKIMVERIFY environment variable. A conservative set of letters is FGHIKLMNOQR‐
TUVWjp. Reject permanently 3PS, FAILURE, SYNTAX, SIGNATURE_BAD, SIGNATURE_EXPIRED, SELECTOR_INVALID, GRANULARITY_MISMATCH, SELECTOR_KEY_REVOKED, DOMAIN_NAME_TOO_LONG, SELECTOR_PUBLIC_KEY_INVALID,
NO_VALID_SIGNATURES and BODY_HASH_MISMATCH errors, and temporarily SIGNATURE_BAD_BUT_TESTING and DNS_TEMP_FAILURE . Add in S if you want to reject messages that do not have a DKIM signature. You can use
the control files signaturedomains and nosignature domains (See Below) to further fine tune the action to be taken when a mail arrives with no DKIM signature. Note that qmail-dkim always inserts the
DKIM-Status header, so that messages can be rejected later at delivery time, or in the mail reader. In that case you may set DKIMVERIFY to an empty string. If you want to check all message’s From header
in signature set the UNSIGNED_FROM environment variable to an empty string. If you want to check messages without signed subject header, set UNSIGNED_SUBJECT environment variable. If you want to honor
body lengh tag (l=), set HONOR_BODYLENGTHTAG environment variable.
qmail-dkim supports signing practice which can be additonall checked when a signature verifcation fails –
SSP – Sender Signing Practice
and
ADSP – Author Domain Signing Practice.
When a signature fails to verify for a message, you can use SSP/ADSP to determine if the message is suspicious or not. To verify a message against SSP/ADSP, set the DKIMPRACTICE environment variable to
the desired set of letters allowed for DKIMVERIFY environment variable. SSP/ADSP should be used only when signature verification fails. SSP/ADSP should be invoked only when libdkim returns the error
codes (F,G,H,I,J,K,L,M,N,P,Q,R,S,T,U,V,W,X) for signature verification. In case you want to test against SSP/ADSP only for DKIM_NO_SIGNATURE and DKIM_NO_VALID_SIGNATURE set the environment variable DKIM‐
PRACTICE=”ST”. If you want automatic behaviour, set DKIMPRACTICE to an empty string. In this case ADSP/SSP will be used when return code matches “FGHIJKLMNPQRSTUVWX”. qmail-dkim uses ADSP as the default
signing practice. You can override this by setting the SIGN_PRACTICE to ssp, adsp, local (lowercase). if you set SIGN_PRACTICE to local, qmail-dkim will check the domain against the control file signa‐
turedomains (See Below). If the domain is found listed in signaturedomains qmail-dkim will bypass ADSP/SSP and return DKIM_FAIL if signature fails to verify. Setting SIGN_PRACTICE to anything else will
cause qmail-dkim to disable Signing Practice.
If you’ve, uh, patched an App for whatever reason, Catalina can be a bit whiny about it, and tell you the app is damaged and can’t be used.
Simple fix
xattr -cr /Applications/DamagedAppName.app
Usual Caveats – only do this if you’ve modified the App yourself.
9
Apple OS Update Issues
If you’ve been running a beta, or if Apple update is just confuzzled 🙂 this may help.
I was getting an error trying to update to the final version of Catalina – “The requested version of Mac OS is not Available”. Installing and removing the beta profile didn’t help.
If you have this issue, you can reset the Software Update Catalog to defaults by doing the following in terminal:
sudo defaults delete /Library/Preferences/com.apple.SoftwareUpdate CatalogURLdefaults delete com.apple.SoftwareUpdate CatalogURLsoftwareupdate --clear-catalog
The last one will warn about being deprecated, but still works.
Check software update again, and you should be able to download updates again.
Have issues with slow loading times for right click, open with menu on OSX?
Copy and paste the below to resolve –
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/LaunchServices.framework/Versions/A/Support/lsregister -kill -seed -r -f -v -domain local -domain user -domain system
Ignore any errors, as it re-removes and re-registers registered context menu’s – once completed, right click menu’s will be back to their fast speed.
I bought a Phicomm R1 Speaker for 150RMB delivered, its supposed to have Wifi and a config app, but the App registration is apparently broken.
The Phicomm R1 speaker has Android installed, unfortunately the configuration app for the speaker is no longer working as noted, so you can only use Bluetooth unless you hack it (Bluetooth is available via a triple press of the top button).
For some crazy reason, the speaker has a fairly decent cpu, and is running Android (albeit without a display, which is annoying, but not completely unfixable); we can connect via adb.
Download adb tools here – https://www.xda-developers.com/install-adb-windows-macos-linux/ and stick in your path.
Set the speaker to Wifi (long press of the top button), and connect to the Phicomm_R1_xxx network.
Mine setup a network on 192.168.43.0/24, with a gateway of 192.168.43.1
adb connect 192.168.43.1:5555
adb shell ls -al
drwxr-xr-x root root 2016-01-21 16:50 acct
lrwxrwxrwx root root 2016-01-21 16:50 bcm4329_cybertan.hcd -> /etc/bluez/bcm432x/BCM4329B1_002.002.023.0389.0000_Cybertan-Foxconn_Cls2_extLNA_EDRmaxInputLev+PeakDEVM_NT.hcd…
-rw-r--r-- root root 148936 1970-01-01 08:00 rk30xxnand_ko.ko.3.10.0
drwx------ root root 2018-04-28 10:50 root
-rw-r--r-- root root 252134 1970-01-01 08:00 vcodec_service.koYup, that worked!
lrwxrwxrwx root root 2016-01-21 16:50 vendor -> /system/vendor
Ok, so we can see the thing at least! Lets get some screen viewing software installed. I’m on OSX, so its a simple brew install..
This seems to work reasonably well – https://github.com/Genymobile/scrcpy
brew install scrcpy
#load ADB first as above on the default unconfigured wifi ip
adb connect 192.168.43.1:5555
scrscpy
You should now be able to see the device display, and the internal app called Pandora. The pandora app is a rather useless one – it basically doesn’t work. So ignore..
We need to install other tools.
#allow any app install
adb shell settings put secure install_non_market_apps 1
Next up, configure wifi on the thing!
#install adb wifi tool
wget https://github.com/steinwurf/adb-join-wifi/releases/download/1.0.1/adb-join-wifi.apk
adb push adb-join-wifi.apk /data/local/tmp/adb-join-wifi.apk
adb shell /system/bin/pm install -t /data/local/tmp/adb-join-wifi.apk
#change YOURSSID, and YOURWIFIPASS as appropriate..
adb shell am start -n com.steinwurf.adbjoinwifi/com.steinwurf.adbjoinwifi.MainActivity -e password_type WPA -e ssid YOURSSID -e password YOURWIFIPASS
It will hopefully setup the wifi. You’ll need to wait for it to ‘timeout’ and tell you wifi setting failed; it will then connect to your normal wifi as set above.
Once on your ‘normal’ wifi, you can adb connect again to the normal ip.
I installed airpin.apk to setup Airplay, now I can connect to the speaker in iTunes, and play. Good enough!
It can be downloaded here – http://www.waxrain.com/product_en.html
Install in a similar manner as other apk’s, then use screen mirroring to config the name.
I called mine phicomm
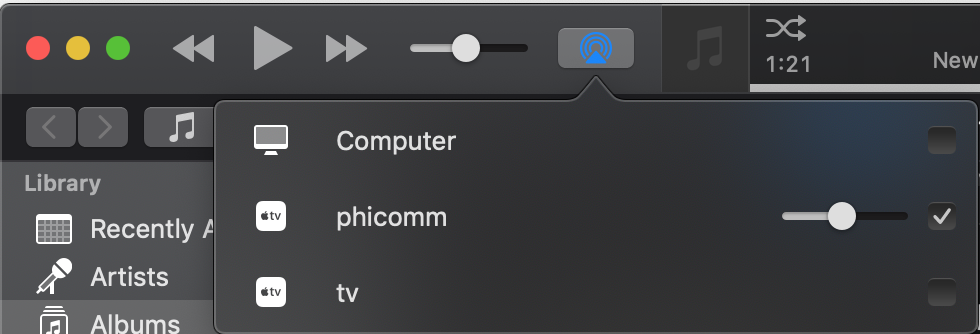
#copy and install airpin APK
adb push AirPin.apk /data/local/tmp/AirPin.apk
adb shell /system/bin/pm install -t /data/local/tmp/AirPin.apk
#run the screen mirroring to configure directly on the device
scrcpy
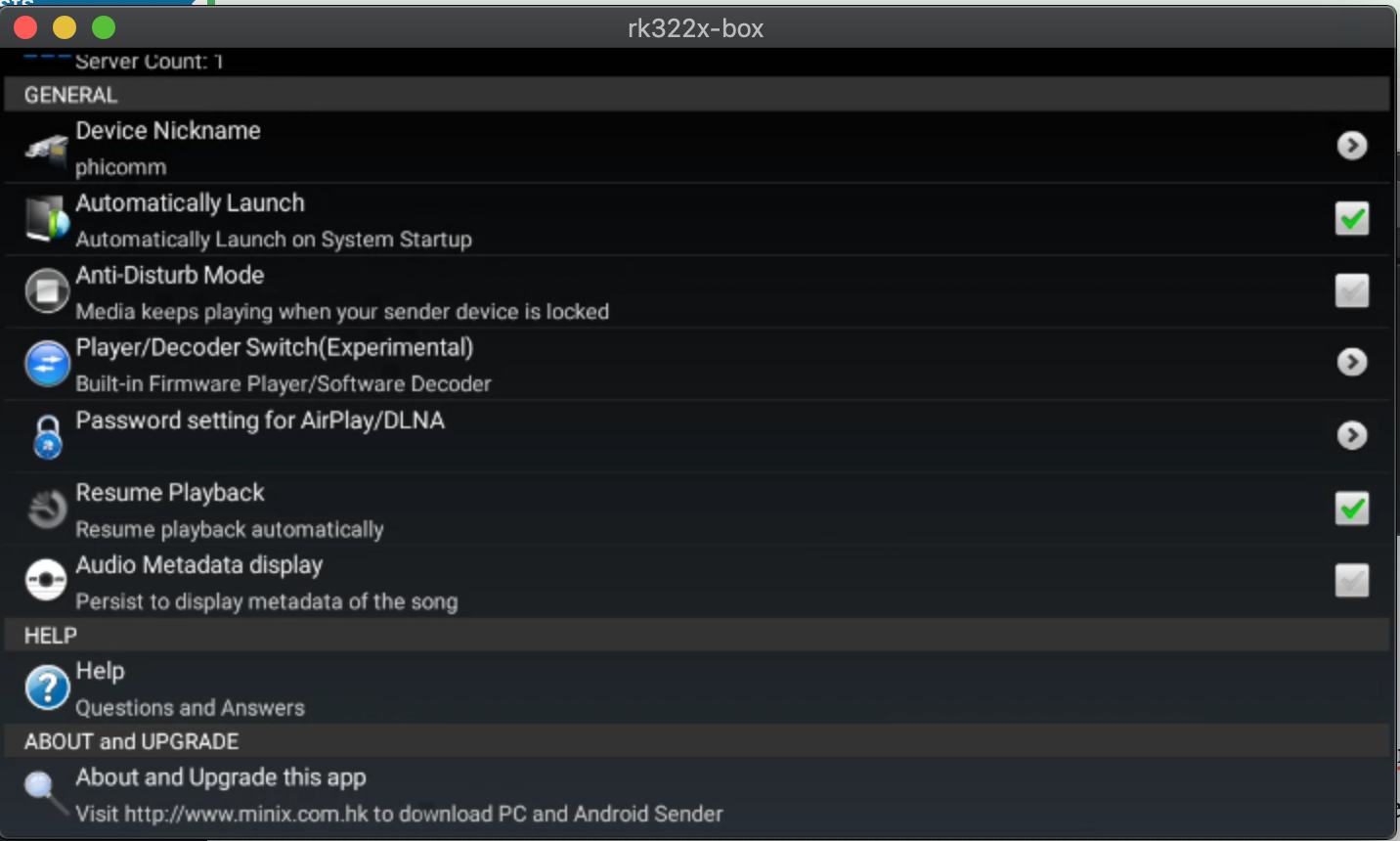
You can go further and remove the Xiao Xun (小讯) listening software, and install something else, but I haven’t bothered (yet). Mine is still unconfigured.
This is detailed in Chinese over here –
https://www.right.com.cn/forum/thread-855587-1-5.html
6
Mail Server Updates
The mail software has been completely revamped to support additional security precautions.
Failed logins will be blocked by ip address for 1 hour. (5 fails to trigger a 1hr block)
Senders can only send mail from their authenticated email address.
Outgoing mail is now also inspected for spam, if tests fail, sending will fail.
DKIM signing is now possible, we are in the process of implementation and testing.
SSL connections are now set to a minimum of TLS1.2 and 2048bit encryption, as per internet standards.
Support for connecting to servers still using old insecure protocols has been deprecated (i.e. not supported anymore).
The protocol insecurity issue is explained in more detail here –
https://weakdh.org
This has impacted some deliveries to outdated servers, which still use outdated software.
We can resolve these issues on a case by case basis if you forward support the relevant bounce messages.
If you see bounce messages with errors similar to this –
SSL routines:tls_process_ske_dhe:dh key too small;
SSL routines:ssl_choose_client_version:unsupported protocol;
The recipients server’s SSL key setup (the key they use for encryption for their mail server) is an issue.
Their keys are too small, and vulnerable to eavesdropping, and ideally need to be updated, as their communications are vulnerable.
30
Cert updates
Certificates for *.computersolutions.cn have been updated to use letsencrypt from April 2019 onward.
22
DNS Updates
As part of our DNS migration in mid 2016 (June / July last year), we asked all our clients to update their DNS to the below servers.
ns1.digitalocean.com
ns2.digitalocean.com
ns3.digitalocean.com
Note that as of today (22nd Feb 2017), our previous DNS servers are now offline, and will no longer resolve.
If you are having issues with email and website hosting today (22nd Feb 2017), please ensure that your DNS has been updated as requested.
This will only affect clients that maintain their own DNS, if your services are managed by us, this was done last year.
If you are unsure on how to proceed, please contact us.
Archives
- November 2024
- November 2019
- October 2019
- August 2019
- April 2019
- February 2017
- September 2016
- June 2016
- May 2016
- September 2015
- August 2015
- June 2015
- April 2015
- December 2014
- October 2014
- September 2014
- July 2014
- June 2014
- April 2014
- October 2013
- July 2013
- May 2013
- April 2013
- March 2013
- January 2013
- December 2012
- October 2012
- August 2012
- July 2012
- June 2012
- May 2012
- April 2012
- March 2012
- December 2011
- November 2011
- October 2011
- September 2011
- July 2011
- May 2011
- April 2011
- March 2011
- February 2011
- January 2011
- December 2010
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
- February 2010
- January 2010
- December 2009
- November 2009
- October 2009
- May 2009
- April 2009
- March 2009
- February 2009
- January 2009
- December 2008
- November 2008
- October 2008
- September 2008
Categories
- Apple
- Arcade Machines
- Badges
- BMW
- China Related
- Cool Hunting
- Exploits
- Firmware
- Food
- General Talk
- government
- IP Cam
- iPhone
- Lasers
- legislation
- MODx
- MySQL
- notice
- qmail
- requirements
- Reviews
- Service Issues
- Tao Bao
- Technical Mumbo Jumbo
- Things that will get me censored
- Travel
- Uncategorized
- Useful Info


